Content
# MCP-SecurityTools Introduction
**MCP-SecurityTools is an open-source project focused on collecting and updating MCPs in the field of network security, aiming to aggregate, organize, and optimize various security tools, technologies, and practical experiences related to MCP.**
| mcp name | Introduction |
| ------------------------------------------------------------ | ------------------------------------- |
| [uncover-MCP](#一uncover-mcp使ai具有调用fofashodan能力) | Enables AI to call FOFA/SHODAN. |
| [ENScan_GO-MCP](#二enscan_go-mcp使ai具有一键信息收集能力) | Enables AI to perform one-click information gathering. |
| [VirusTotal-MCP](#三virustotal-mcp使ai具有virustotal的安全分析能力) | Enables AI to perform VirusTotal security analysis. |
| [cloudsword-MCP](#四cloudsword-mcp使ai具有云安全能力) | Enables AI to have cloud security capabilities, one-line R penetrates the cloud environment. |
| [ZoomEye-MCP](#五zoomeye-mcp使ai具有查询zoomeye来获取网络资产信息) | Enables AI to query ZoomEye to obtain network asset information |
| [AWVS-MCP](#六awvs-mcp使ai具有调用awvs进行漏洞扫描能力) | Enables AI to call AWVS for vulnerability scanning |
| GhidraMCP | To be updated, planned |
| IDA-MCP | To be updated, planned |
| Nmap-MCP | To be updated, planned |
## Zero: Introduction
MCP (Model Context Protocol) is an open protocol for standardizing how applications provide context to LLMs. You can think of MCP as a USB-C interface for AI applications. Just as USB-C provides a standardized way for devices to connect various peripherals and accessories, MCP provides a standardized way for AI models to connect to different data sources and tools.
### 0.1 Why choose MCP?
MCP helps you build agents and complex workflows on top of LLMs. LLMs often need to integrate with data and tools, and MCP provides:
- A list of pre-built integrations that your LLM can directly access
- Flexibility to switch between different LLM providers and vendors
- Best practices for securing data in your infrastructure
### 0.2 Overall Architecture
Essentially, MCP follows a client-server architecture, where a host application can connect to multiple servers:
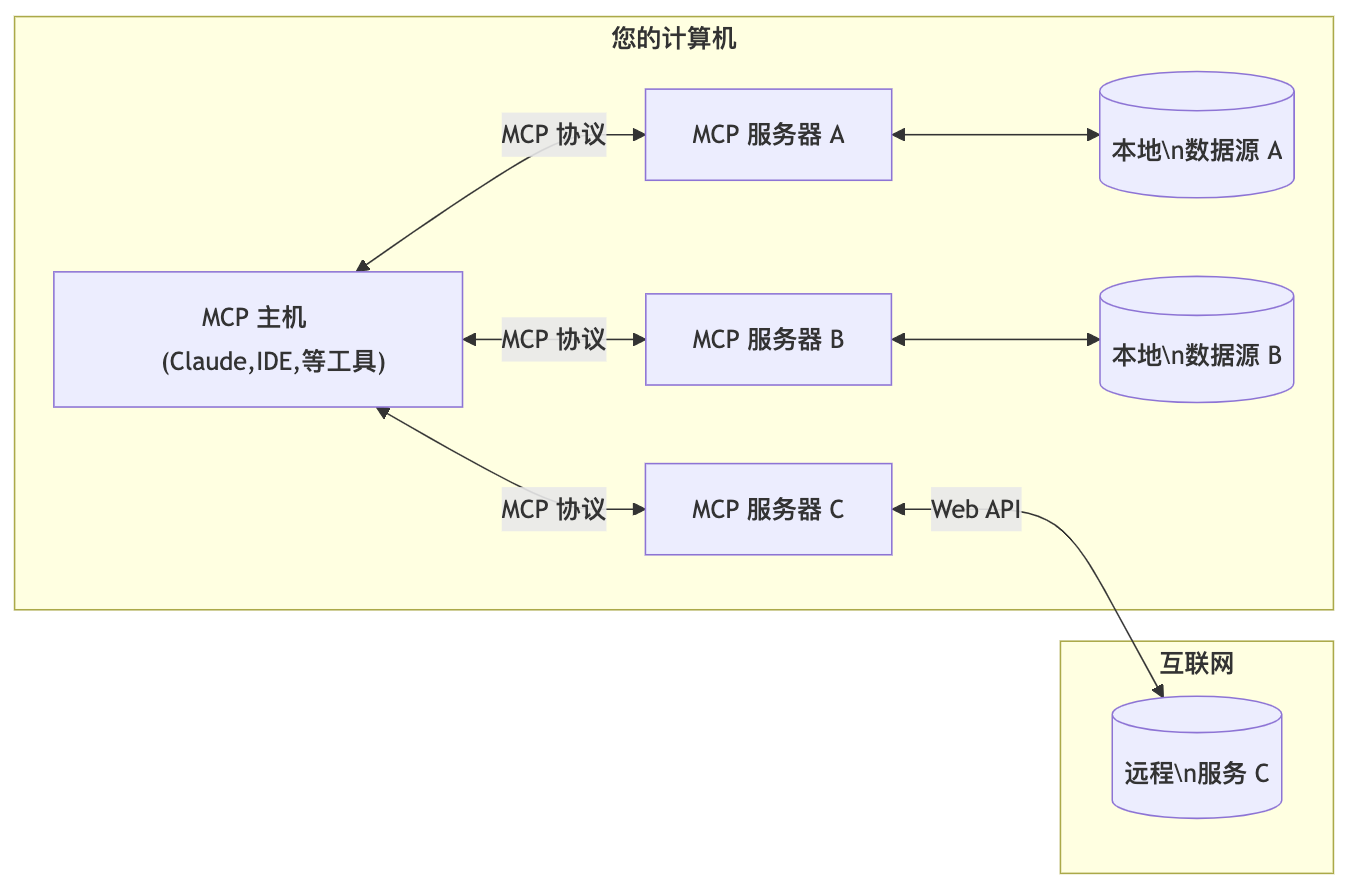
**MCP Host**: Programs like Claude, Cherry Studio client, IDE, or AI tools that want to access data through MCP.
- **MCP Client**: A protocol client that maintains a 1:1 connection with the server
- **MCP Server**: A lightweight program that exposes specific functionality through a standardized model context protocol
- **Local Data Source**: Computer files, databases, and services that the MCP server can securely access
- **Remote Services**: External systems provided over the Internet that the MCP server can connect to (e.g., via API)
---
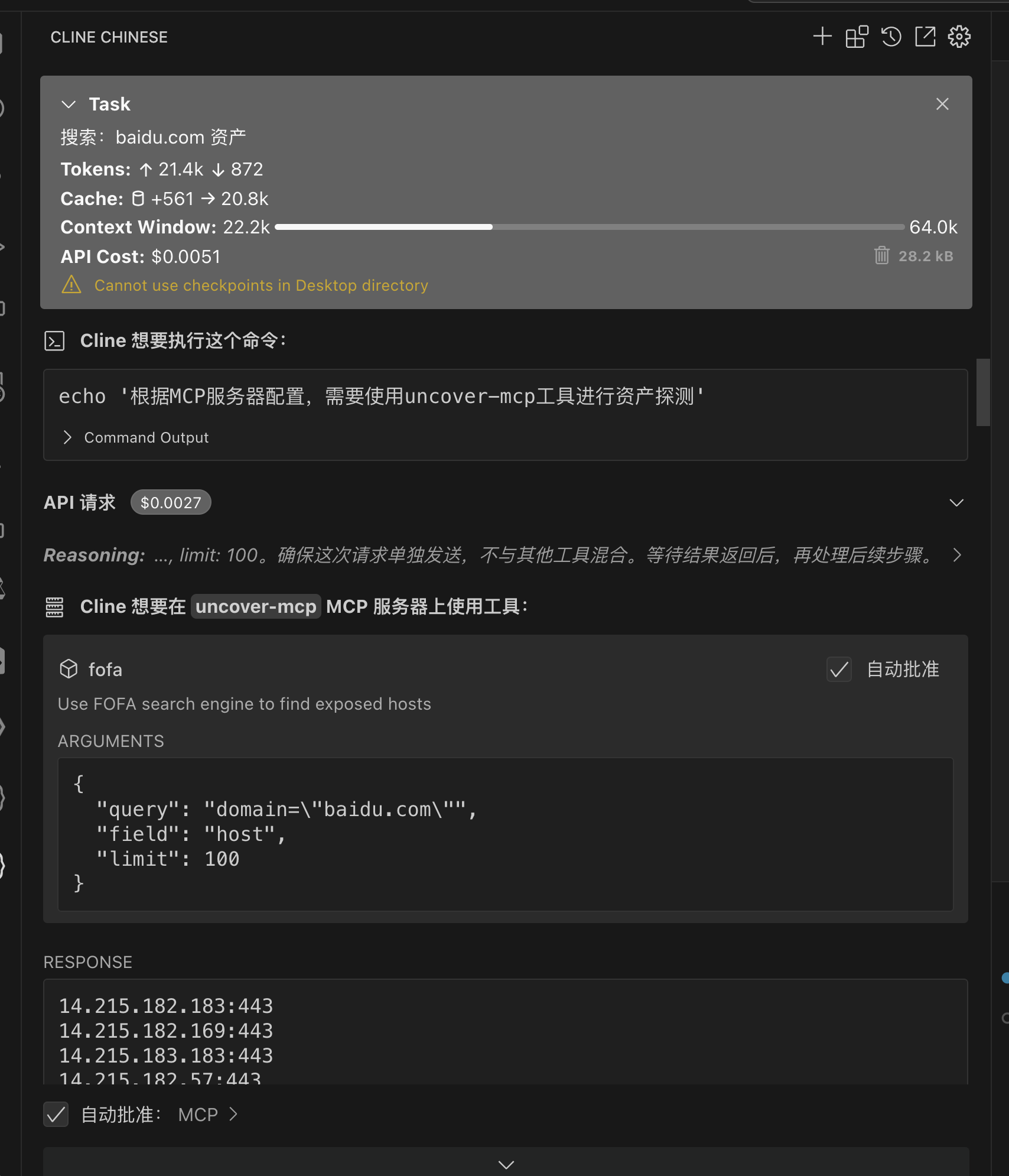
## One: uncover-MCP(Enables AI to call FOFA/SHODAN)
**Project Address:** `https://github.com/Co5mos/uncover-mcp`
### 1.1 Compilation Instructions
```
# Clone the repository
git clone https://github.com/Co5mos/uncover-mcp
cd uncover-mcp
# Build the project (requires Go 1.21 or higher)
go build -o uncover-mcp ./cmd/uncover-mcp
# It is recommended to use the author's build file: https://github.com/Co5mos/uncover-mcp/releases/tag/v0.0.1-beta
```
### 1.2 Usage
**Run as an MCP service instance:**
```json
{
"mcpServers": {
"uncover-mcp": {
"command": "./uncover-mcp",
"args": [],
"env": {
"SHODAN_API_KEY": "",
"FOFA_EMAIL": "",
"FOFA_KEY": ""
}
}
}
}
```
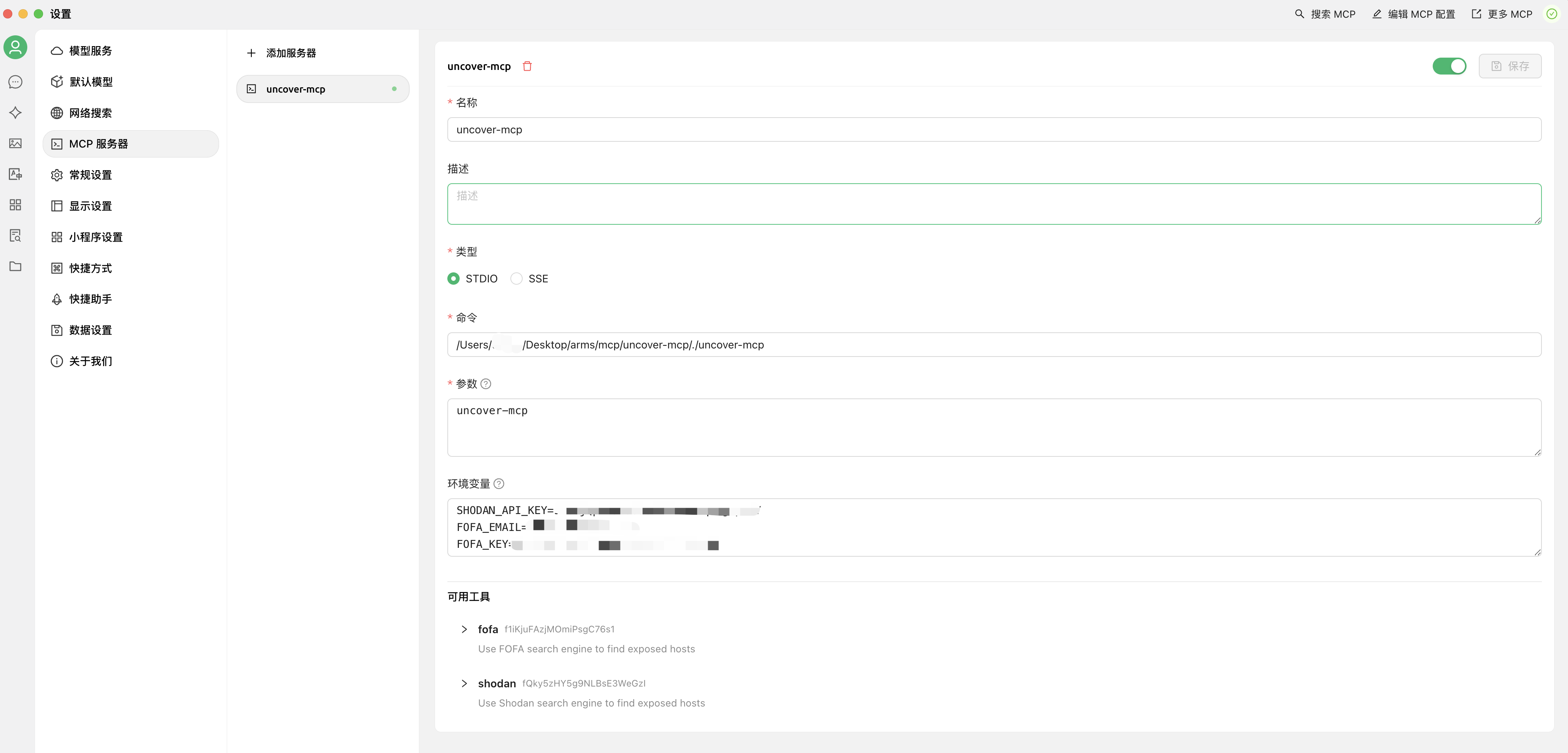
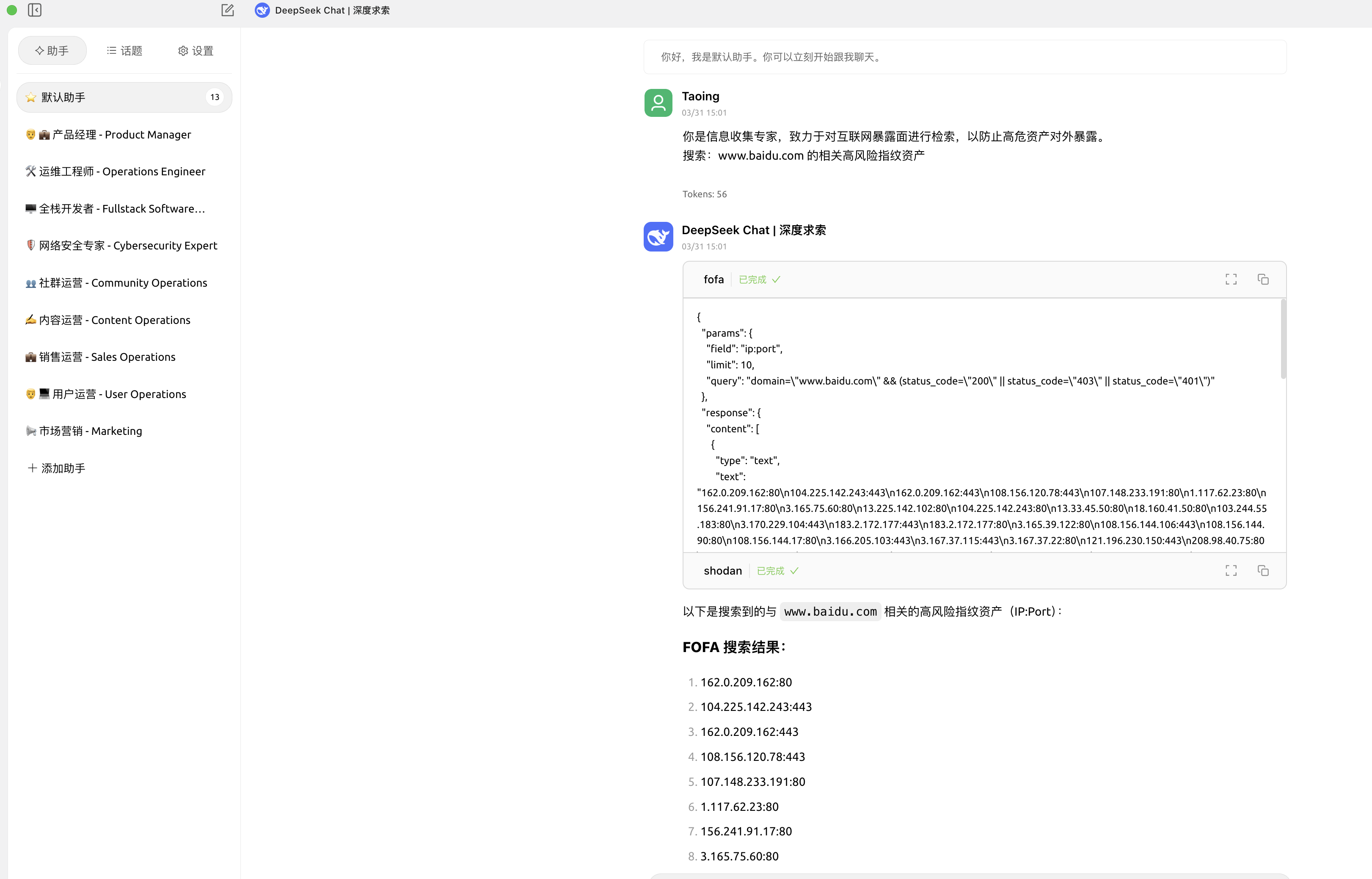
**Use in Cherry Studio**
> See the Cherry StudioMCP tutorial for details: `https://docs.cherry-ai.com/advanced-basic/mcp`
```json
{
"mcpServers": {
"uncover-mcp": {
"name": "uncover-mcp",
"isActive": true,
"command": "You compile the uncover-mcp binary file",
"args": [
"uncover-mcp"
],
"env": {
"SHODAN_API_KEY": "xxxxxxxxxx",
"FOFA_EMAIL": "xxxxxxxxxx",
"FOFA_KEY": "xxxxxxxxxx"
}
}
}
}
```
**Use in cline**
```json
{
"mcpServers": {
"uncover-mcp": {
"command": "You compile the uncover-mcp binary file",
"args": [],
"env": {
"SHODAN_API_KEY": "xxxxxxxxxx",
"FOFA_EMAIL": "xxxxxxxxxx",
"FOFA_KEY": "xxxxxxxxxx"
},
"autoApprove": [
"fofa"
]
}
}
}
```
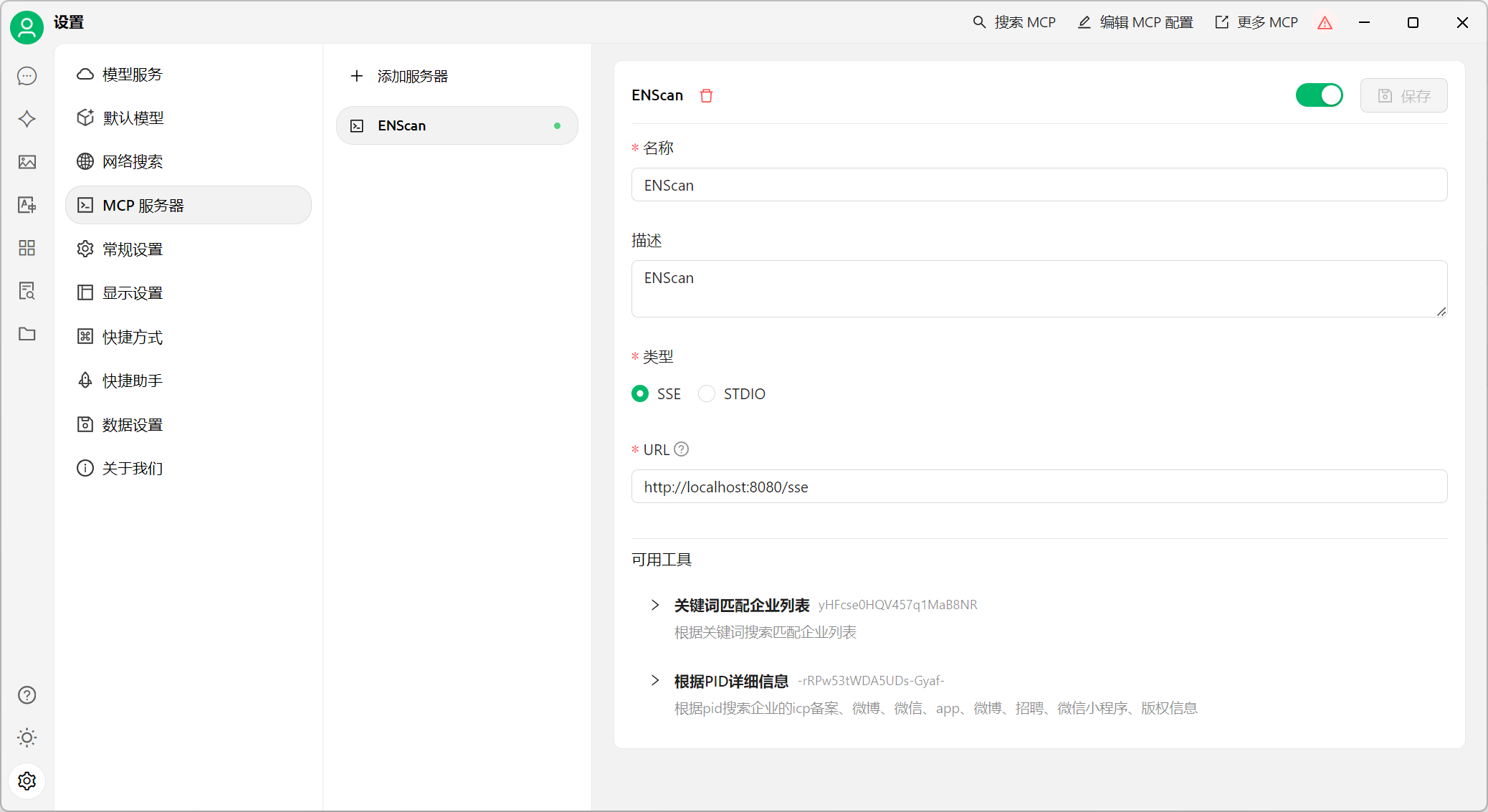
## Two: ENScan_GO-MCP(Enables AI to perform one-click information gathering)
**Project Address:** `https://github.com/wgpsec/ENScan_GO`
### 2.1 Using MCP
Enable the MCP server, which will listen on `http://localhost:8080` locally.
```
./enscan --mcp
```
**Example configuration with Cherry Studio**
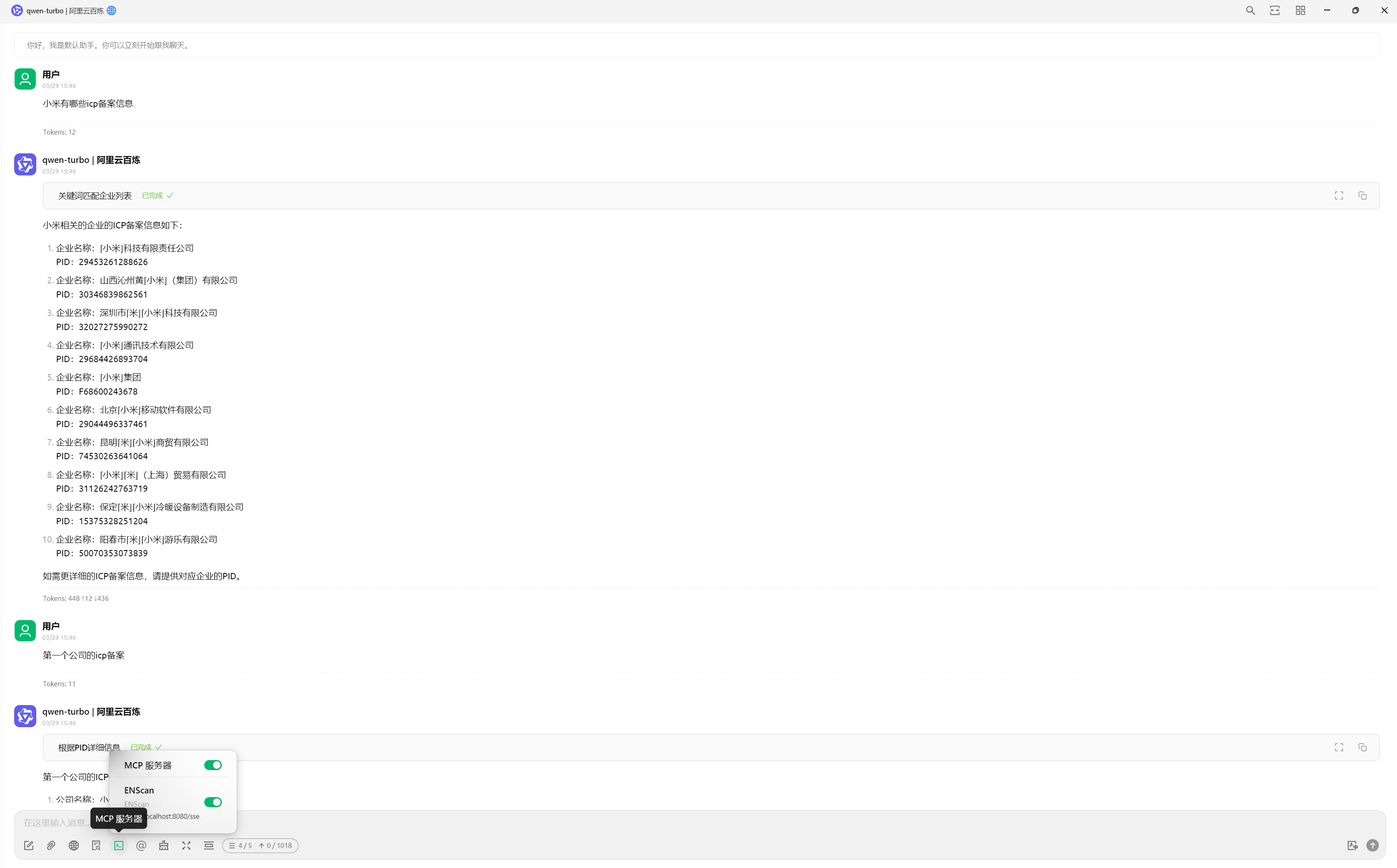
## Three: VirusTotal-MCP(Enables AI to perform VirusTotal security analysis)
**Project Address:** ` https://github.com/BurtTheCoder/mcp-virustotal·`
### 3.1 Compilation Instructions
```txt
# Requires node environment
git clone https://github.com/BurtTheCoder/mcp-virustotal.git
cd mcp-virustotal
npm install
npm run build
```
### 3.2 Usage
**Use in Cherry Studio**
> See the Cherry StudioMCP tutorial for details: `https://docs.cherry-ai.com/advanced-basic/mcp`
```json
{
"mcpServers": {
"s4Q9KPP86Ec_MWVfGURLI": {
"isActive": true,
"name": "virustotal-mcp",
"description": "virustotal-mcp",
"command": "node",
"args": [
"--experimental-modules",
"You compile the uncover-mcp binary file"
],
"env": {
"VIRUSTOTAL_API_KEY": "xxxxxxxxxx"
}
}
}
}
```
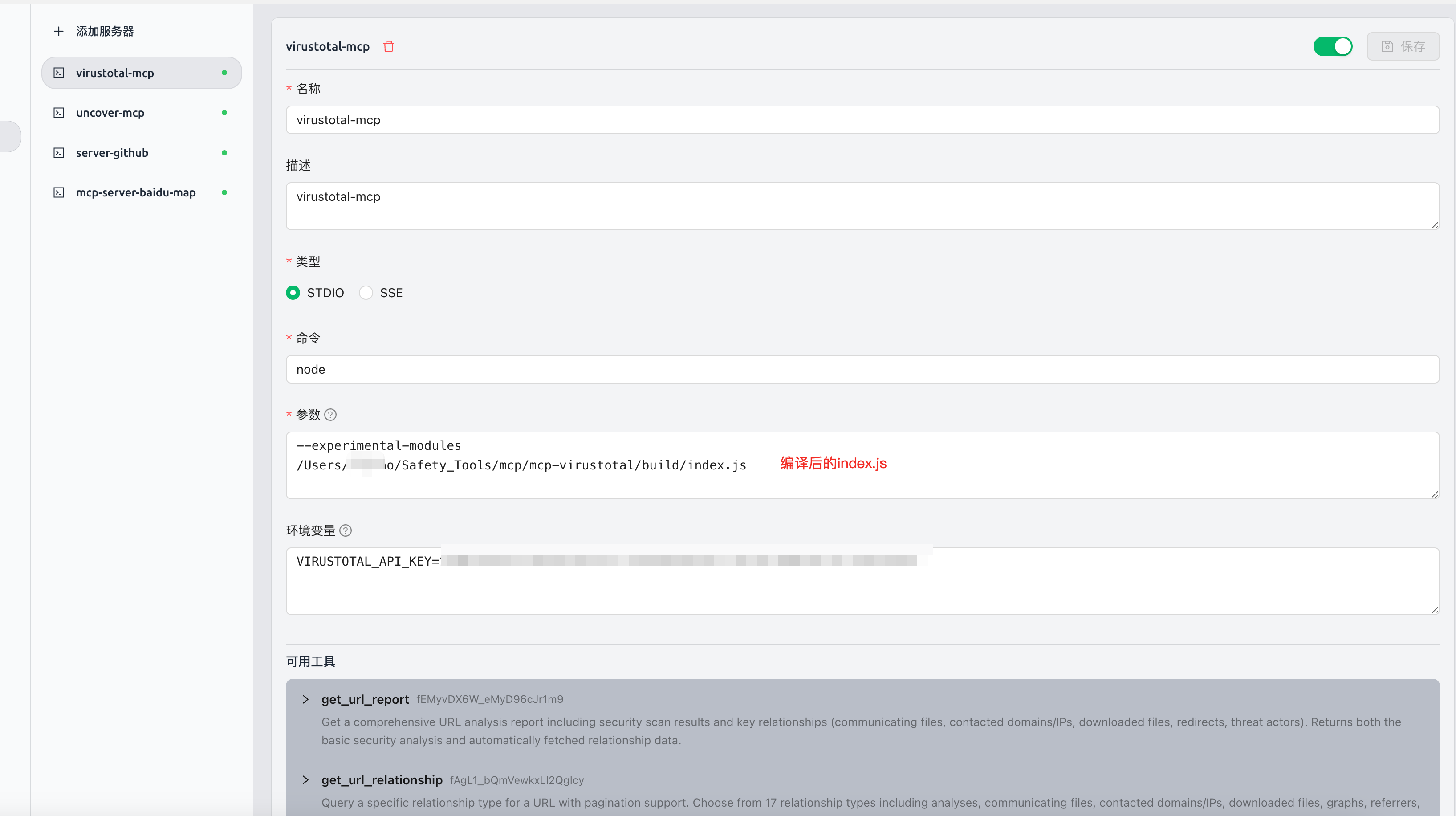
**Use in cline**
```json
{
"mcpServers": {
"virustotal": {
"command": "node",
"args": [
"--experimental-modules",
"You compile the uncover-mcp binary file"
],
"env": {
"VIRUSTOTAL_API_KEY": "xxxxxxxxxx"
},
"autoApprove": [
"get_url_report",
"get_file_report",
"get_url_relationship",
"get_ip_report",
"get_domain_report",
"get_url_relationship",
"get_file_relationship"
]
}
}
}
```
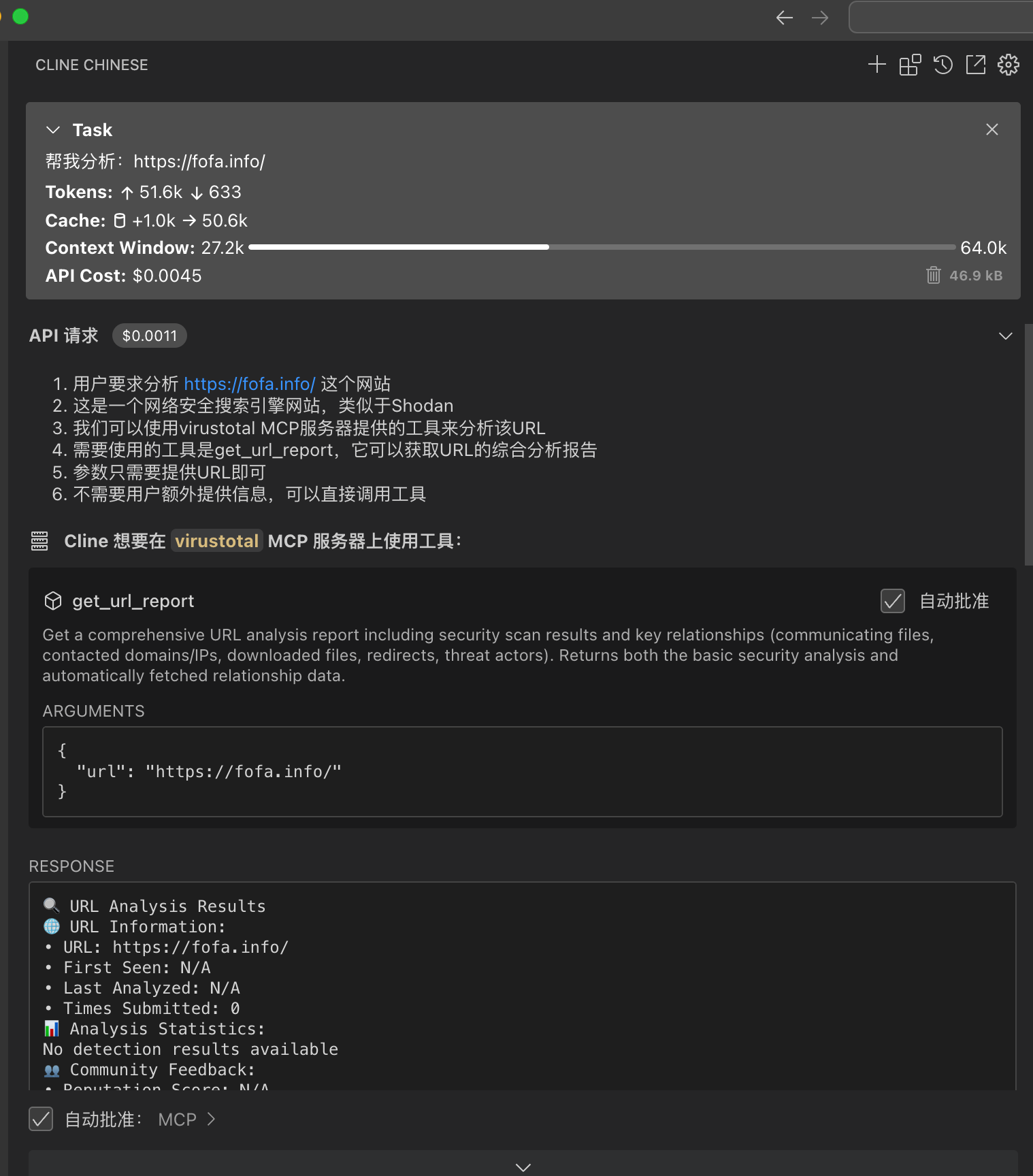
## Four: cloudsword-MCP(Enables AI to have cloud security capabilities)
**Project Address:** ` https://github.com/wgpsec/cloudsword`
> cloudsword supports the MCP protocol from version v0.0.2, supporting SSE and STDIO modes.
Use the command `./cloudsword sse http://localhost:8080` to listen on port 8080 locally.
## 4.1 Usage
**Use in Cherry Studio**
**Currently, testing in cline is not available, will be resolved later**
**SSE Mode**
Taking Chrerry stdio as an example, fill in `http://localhost:8080/sse` to obtain tool information.
```json
{
"mcpServers": {
"iAcI362KsjDNFU_FqZEaO": {
"isActive": true,
"name": "cloudsword-MCP",
"description": "",
"baseUrl": "http://localhost:8080/sse"
}
}
}
```
[](https://github.com/wgpsec/cloudsword/blob/master/static/image-20250401193340509.png)
**STDIO Mode**
```json
{
"mcpServers": {
"iAcI362KsjDNFU_FqZEaO": {
"name": "cloudsword-MCP",
"description": "Enables AI to have cloud security capabilities",
"isActive": true,
"command": "You compile the uncover-mcp binary file",
"args": [
"stdio"
]
}
}
}
```
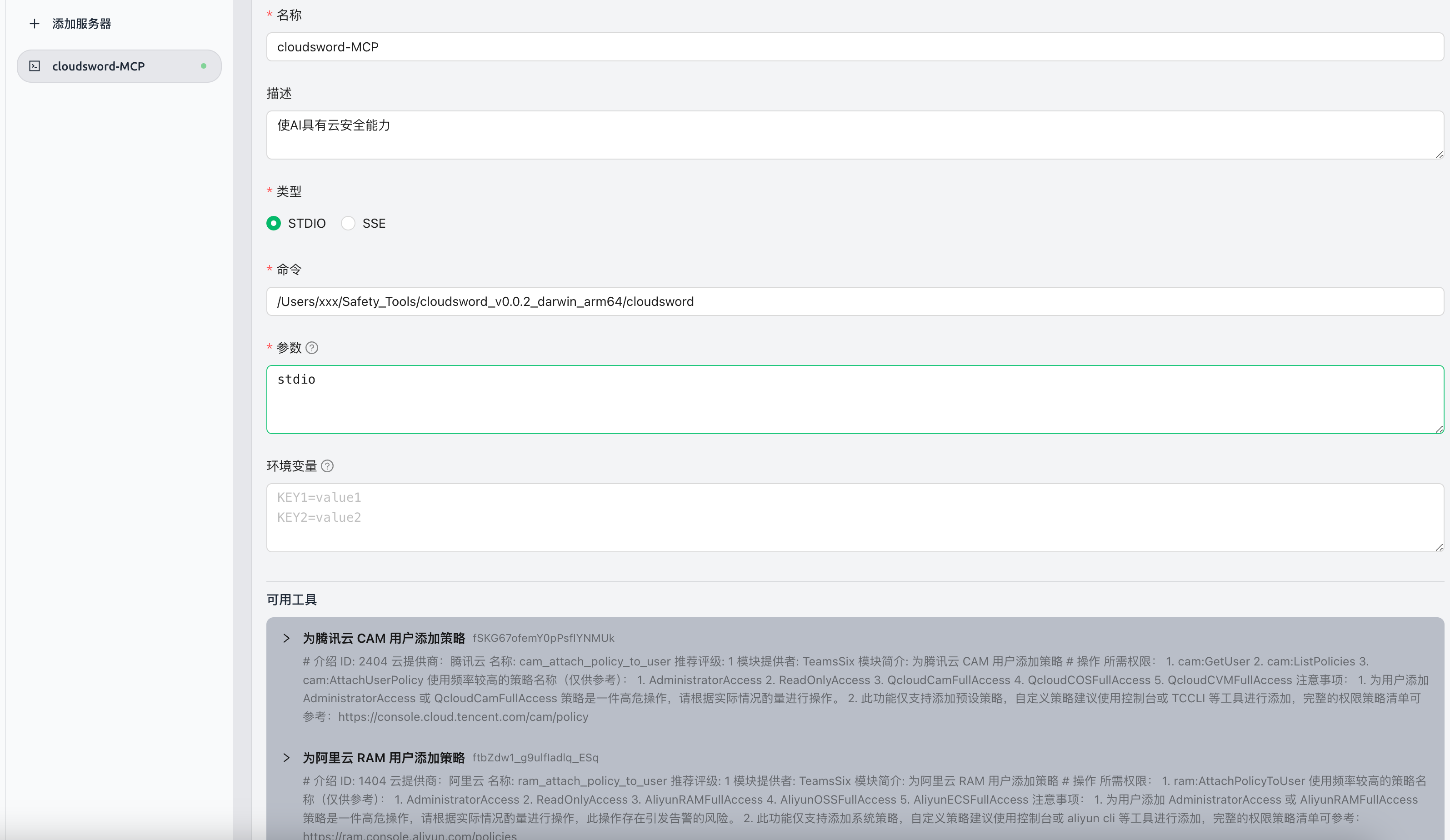
[](https://github.com/wgpsec/cloudsword/blob/master/static/image-20250401193444375.png)
**Usage Example**
[](https://github.com/wgpsec/cloudsword/blob/master/static/image-20250401194214015.png)
## Five: ZoomEye-MCP(Enables AI to query ZoomEye to obtain network asset information)
**Project Address:** `https://github.com/zoomeye-ai/mcp_zoomeye`
> Allows large language models (LLMs) to obtain network asset information by querying ZoomEye using dorks and other search parameters.
**Usage Tutorial:** The official documentation is very detailed `https://github.com/zoomeye-ai/mcp_zoomeye`
## 5.1 Usage
**Use in Cherry Studio**
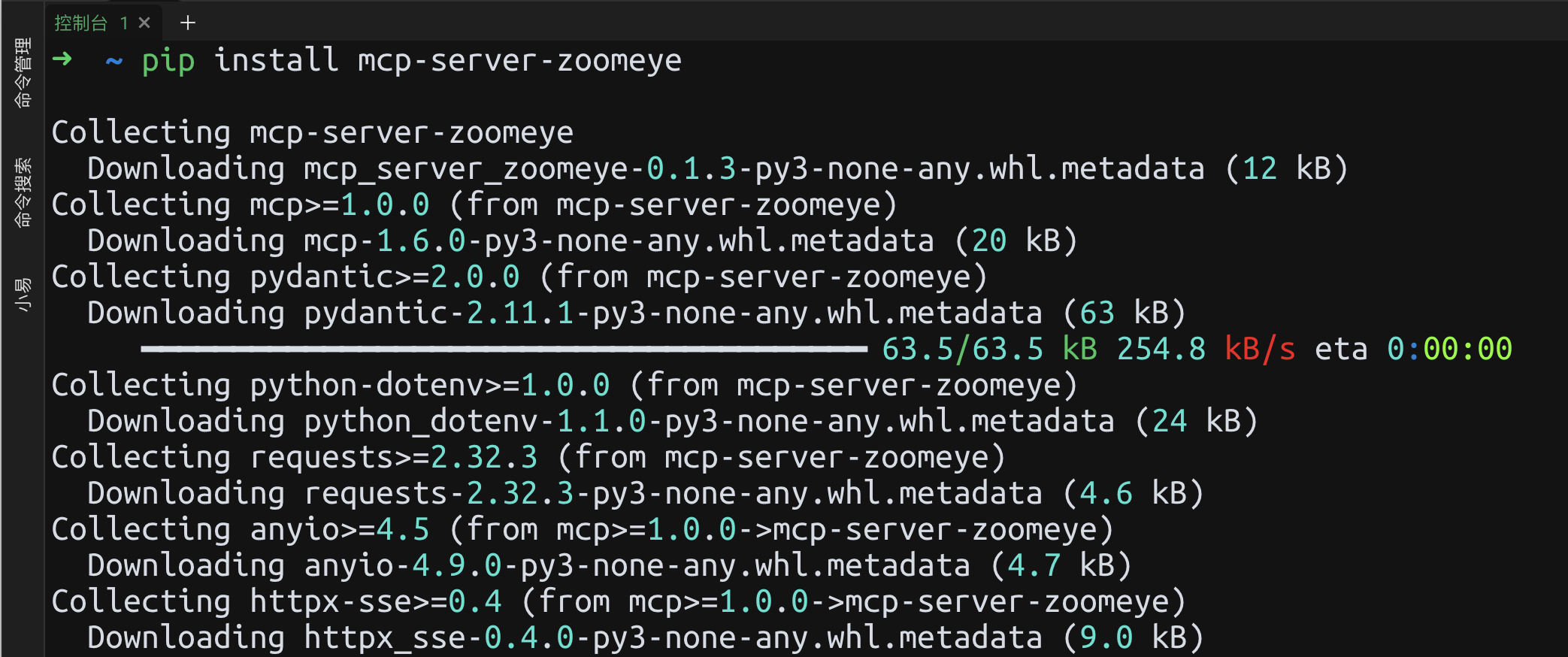
**Installation and Usage**
```
# Install via pip
pip install mcp-server-zoomeye
```
```json
{
"mcpServers": {
"zoomeye": {
"isActive": true,
"name": "zoomeye-MCP",
"description": "zoomeye-MCP",
"command": "uvx",
"args": [
"mcp-server-zoomeye"
],
"env": {
"ZOOMEYE_API_KEY": "xxxxxxxxx"
}
}
}
}
```
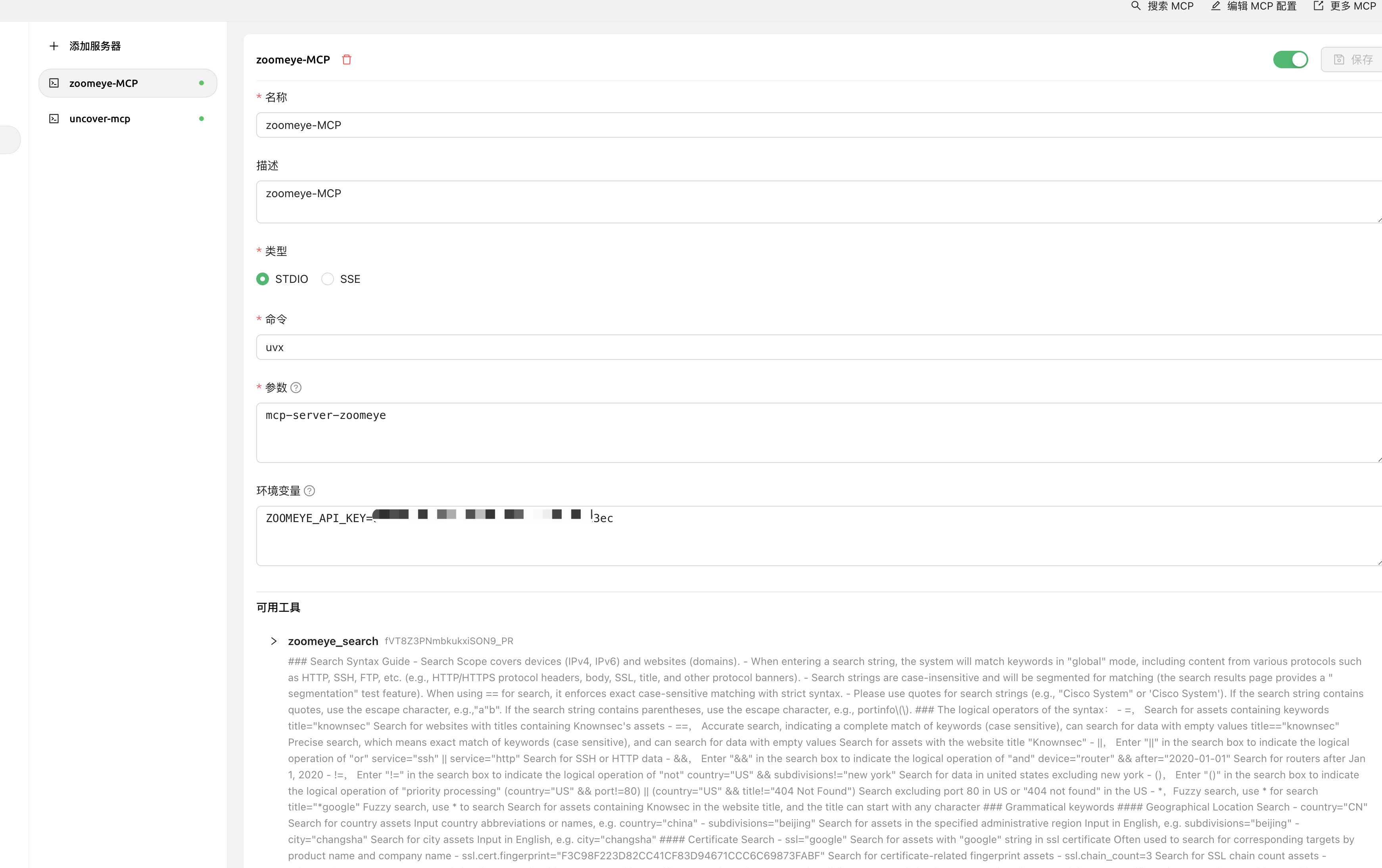
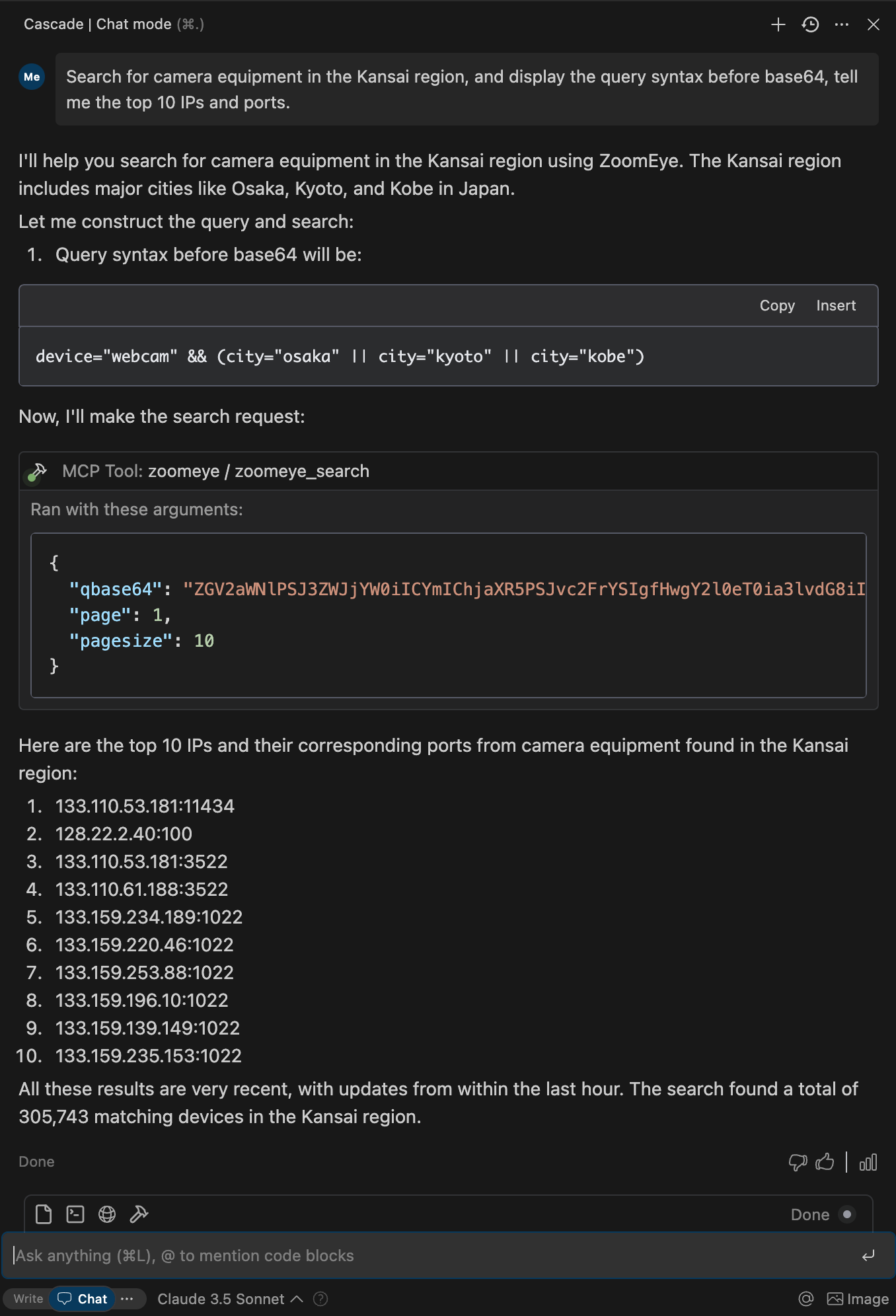
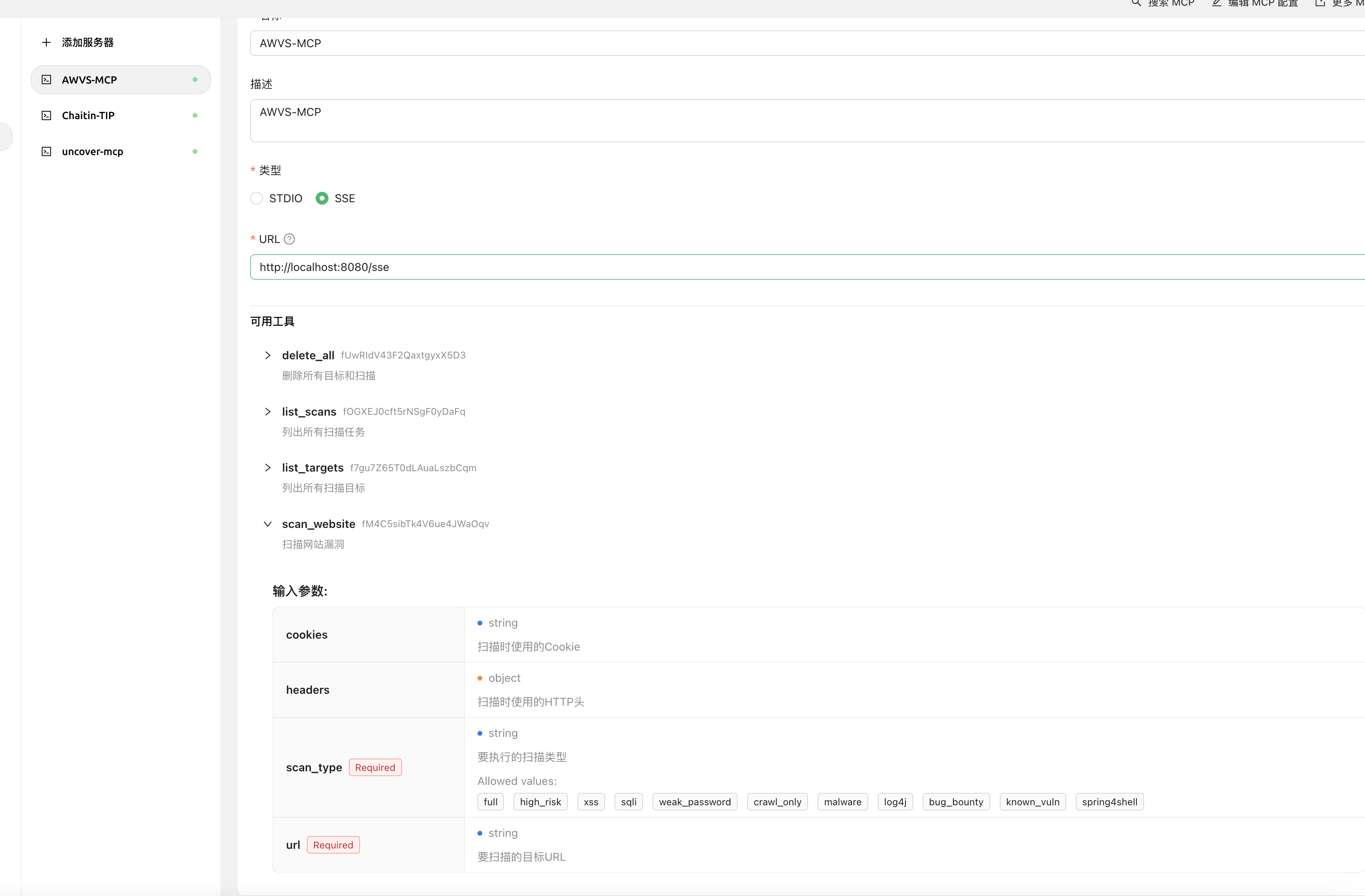
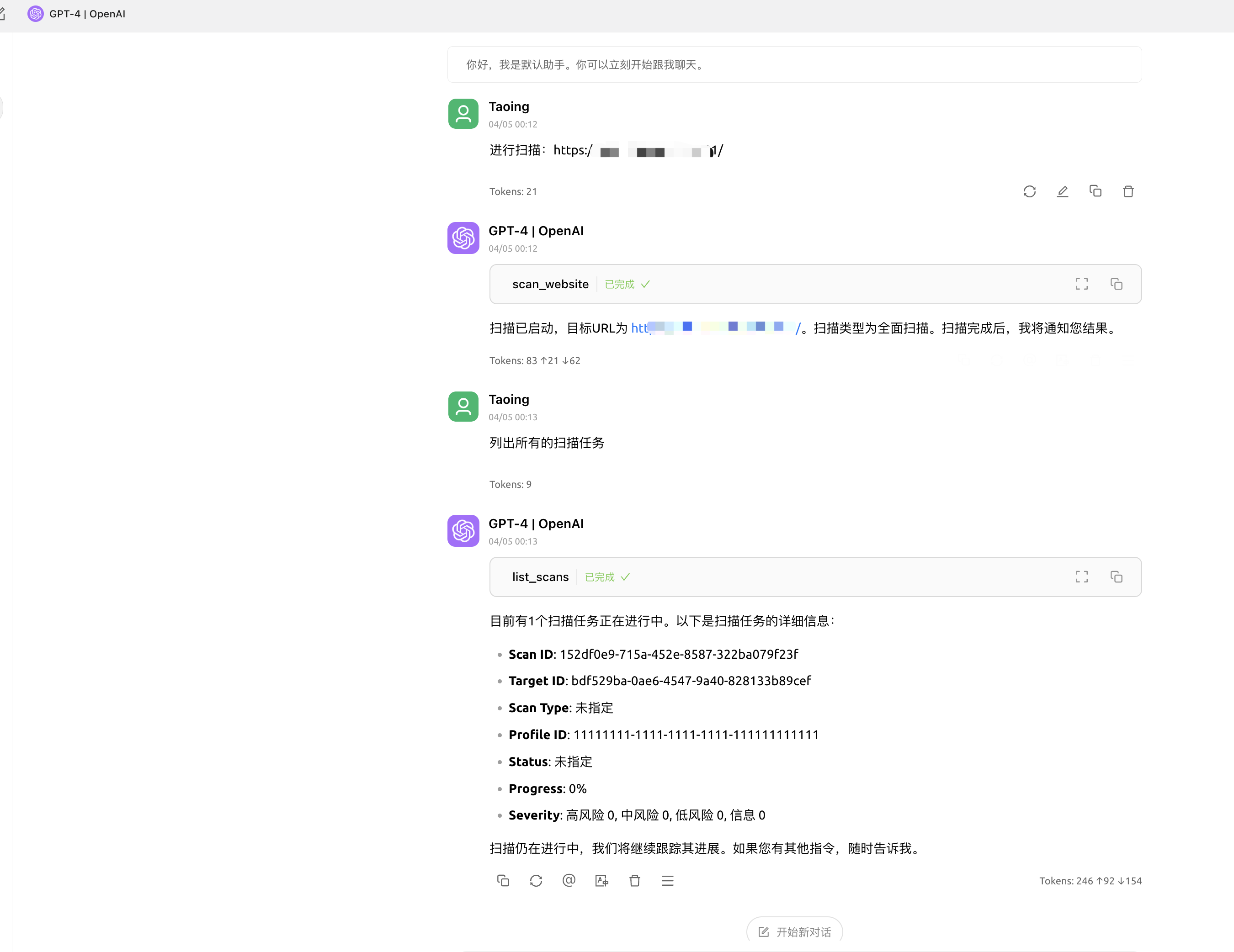
## Six: AWVS-MCP(Enables AI to call AWVS for vulnerability scanning)
**Project Address:** ` https://github.com/Ta0ing/MCP-SecurityTools/tree/main/awvs-mcp`
> Supports SSE and STDIO modes.
Use the command `awvs-mcp sse --port 8080` to listen on port 8080 locally.
## 6.1 Usage
**Use in Cherry Studio**
**SSE Mode**
Taking Chrerry stdio as an example, fill in `http://localhost:8080/sse` to obtain tool information.
Connection Info
You Might Also Like
markitdown
MarkItDown-MCP is a lightweight server for converting URIs to Markdown.

Time
A Model Context Protocol server for time and timezone conversions.

Filesystem
Node.js MCP Server for filesystem operations with dynamic access control.
claude-code-ultimate-guide
A comprehensive guide to mastering Claude Code from beginner to expert.
axon
Graph-powered code intelligence engine — indexes codebases into a knowledge...
mcp-server-youtube-transcript
A server for retrieving YouTube video transcripts and subtitles easily.